Achieving End-to-End Zero Trust
Palo Alto Networks
MAY 29, 2020
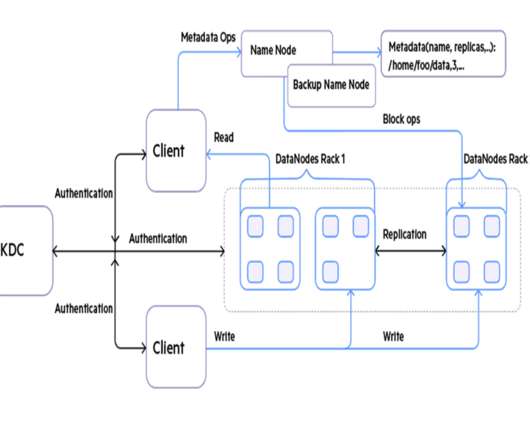
That means that each entity, such as an endpoint, server, VM- or container-based microservice, or Platform-as-a-Service (PaaS), must validate the identity of any endpoint, workload or application that it communicates with as well as scan any content that it sends, receives or maintains at rest for malicious activity. . Applications.

























Let's personalize your content