4 remedies to avoid cloud app migration headaches
CIO
NOVEMBER 29, 2023
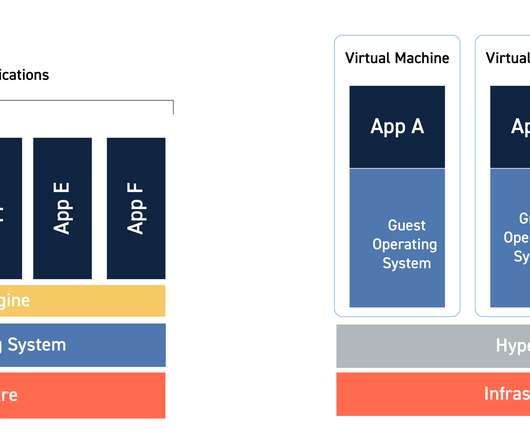
Pablo Del Giudice, cloudops and cybersecurity studio partner at professional services firm Globant, adds that migration is possible if you position your organization correctly. Platform lock-in occurs when you have a complete cloud foundation configuration (resource grouping, policies, RBAC, hybrid connectivity, monitoring, compliance, etc.)



























Let's personalize your content