Huawei’s Vision for Intelligent Networking Unveiled at GITEX Global 2023
CIO
NOVEMBER 7, 2023
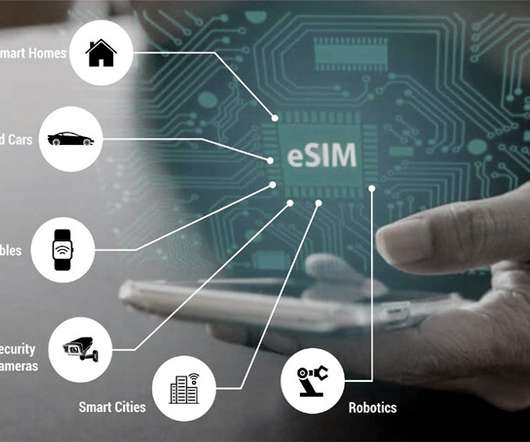
In healthcare, the High-Quality Small and Midsize Hospital Network Solution supports IoT services, facilitating healthcare IoT with improved quality. In the data center domain, Huawei’s Super-Connectivity 400GE CloudFabric Solution steps up to confront the challenges arising from the surging demand for intelligent computing.





















Let's personalize your content