CloudEndure Migration & Disaster Recovery
Datavail
JULY 8, 2020
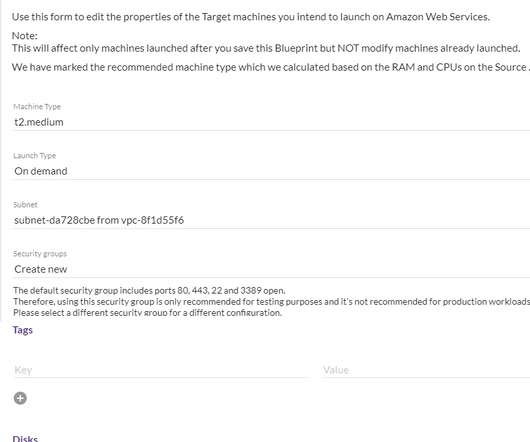
Traditionally, if you want to migrate or set up disaster recovery (DR) for applications or databases on-premise, Google, AWS, etc. Additional CloudEndure nearly provides zero Recovery Point Objective (RPO) and minutes for Recovery Time Objective (RTO). Let’s get started. Contact us to learn more.





















Let's personalize your content