The Security Stage debuts at Disrupt 2023
TechCrunch
APRIL 11, 2023
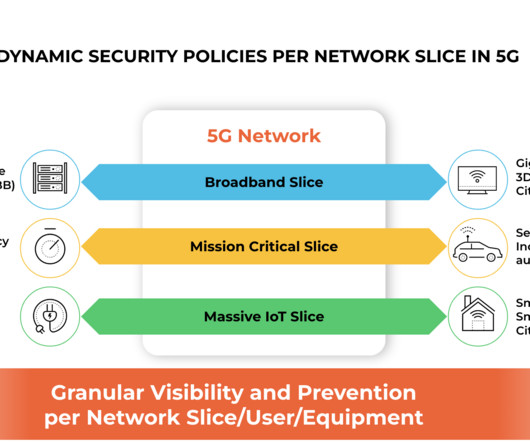
If you haven’t noticed, the internet is frequently on fire. ” Small towns and local governments are largely unable to fend off ransomware attacks on their own. Can governments keep cyberspace safe and protect our information without compromising its values or violating human rights? Just how on fire are we ?























Let's personalize your content