Kentik Detect Alerting: Configuring Alert Policies
Kentik
JULY 11, 2017
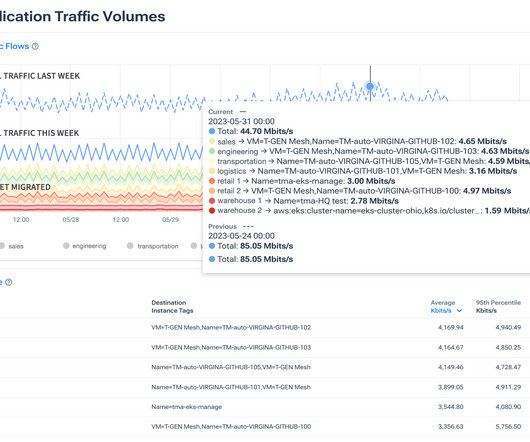
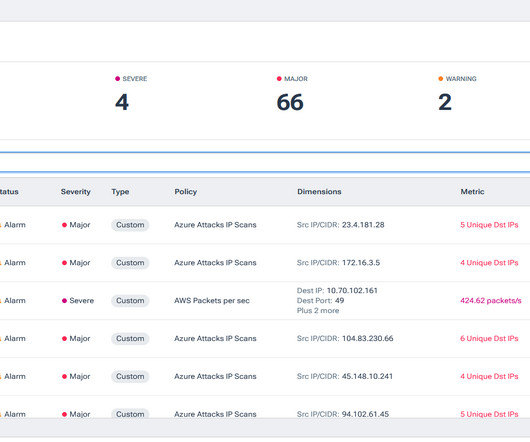
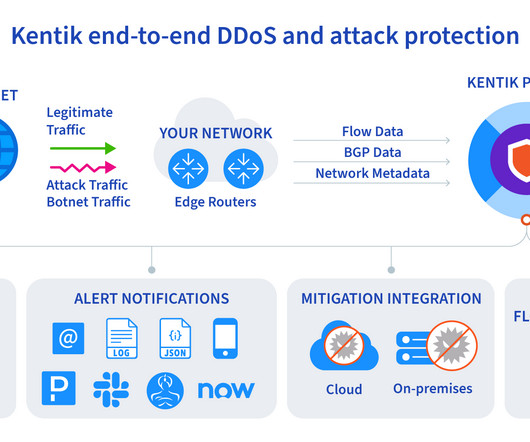
Deep, Powerful Anomaly Detection to Protect Your Network. To stay on top of these changes, you need a comprehensive network visibility solution that includes real-time anomaly detection. To stay on top of these changes, you need a comprehensive network visibility solution that includes real-time anomaly detection.

























Let's personalize your content