Securing Your Metadata from Cloud Heists with Prisma Cloud’s Attack Path Policies
Prisma Clud
SEPTEMBER 26, 2023
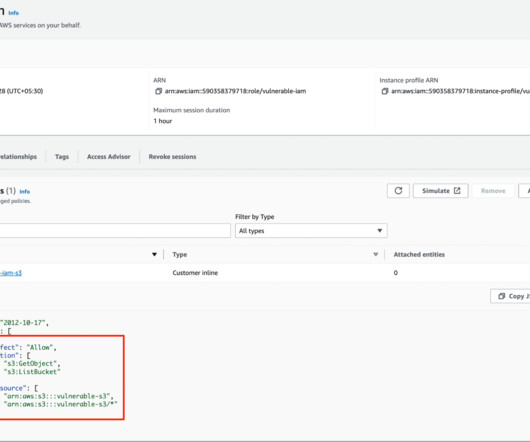
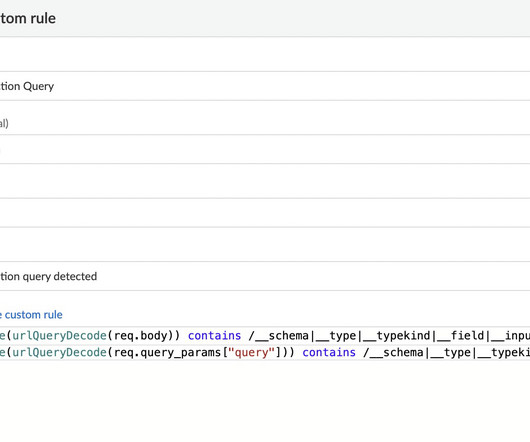
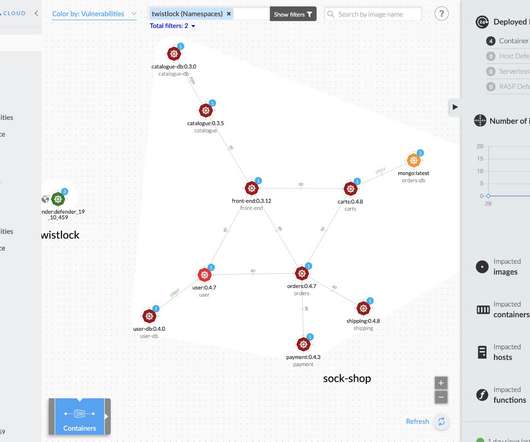
Many businesses today rely on cloud computing, and AWS is a significant player in this space. Its enhanced version, IMDSv2, requires session-oriented requests, adding an extra layer of security. Armed with IAM role credentials, the attacker can make authenticated AWS API requests. Using AWS, though, can be tricky.


































Let's personalize your content