The Power of AI Assistants and Advanced Threat Detection
Palo Alto Networks
APRIL 4, 2024
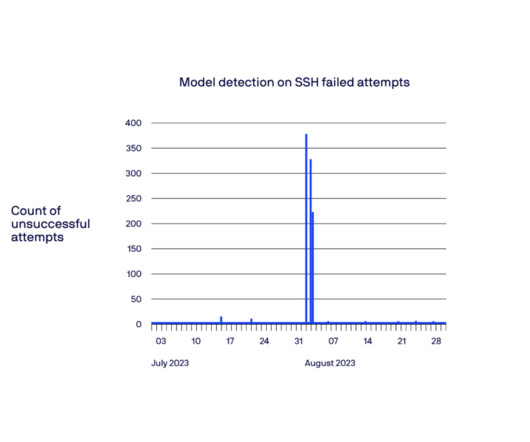
We recently interviewed Mike Spisak, technical managing director with the Proactive Services Creation Team at Unit 42. The ability to distinguish legitimate traffic from malicious traffic and then automatically diverting or taking autonomous action to maintain service availability will become increasingly refined," Spisak explained.



































Let's personalize your content