Fixed wireless access (FWA) is a secure networking option
CIO
DECEMBER 19, 2023
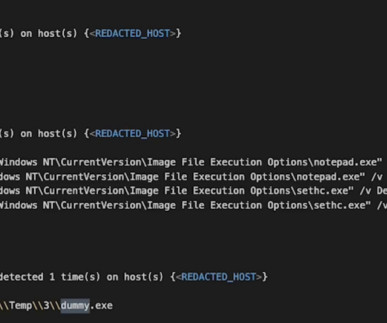
Cyber hygiene best practices include device security , cyber security education , and secure networking strategies. However, outdated operating systems can be more vulnerable to security risks because they may lack the latest security updates and patches, serving as an entry point for hackers to infiltrate networks.




































Let's personalize your content