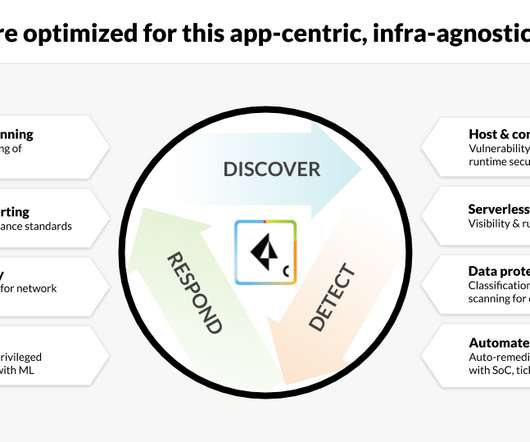
Use custom rules to validate your compliance
Xebia
FEBRUARY 3, 2024
AWS has a lot of controls built in, but what if you need more? AWS Config allows you to create your own rules. AWS has a built-in config rule for this called s3-bucket-logging-enabled. When you enable the AWS Foundational Security Best Practices v1.0.0 With AWS Config you can define InputParameters.











































Let's personalize your content