Why you must extend Zero Trust to public cloud workloads
CIO
NOVEMBER 8, 2023
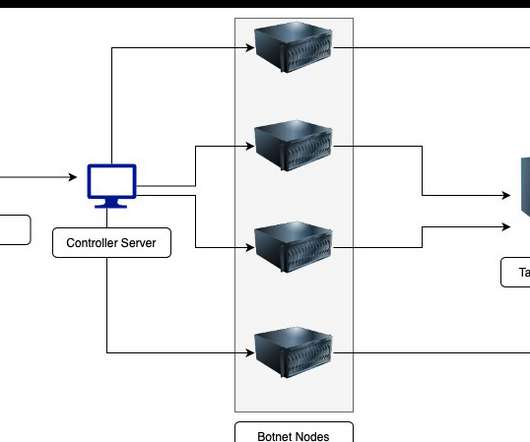
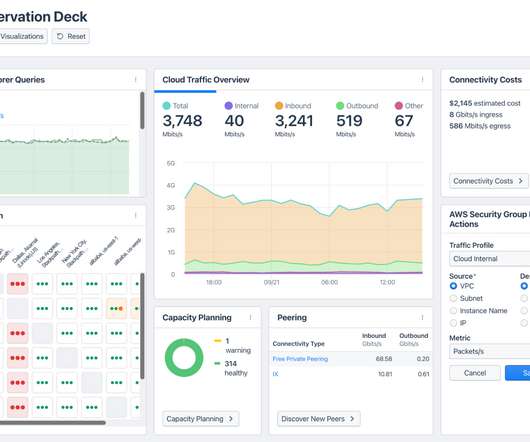
Why securing cloud workloads is an urgent matter In recent years, major cloud service providers encountered 6,000 malware samples actively communicating with them, underlining the magnitude of cloud security challenges. It’s not as simple as just extending traditional firewall capabilities to the cloud. 8 Complexity.




































Let's personalize your content