Cloud PC preps Grant Thornton for hybrid future
CIO
AUGUST 8, 2022
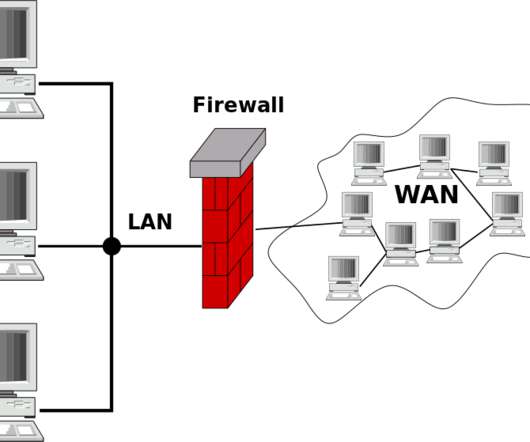
Enterprises that pushed in early to the cloud fared far better than their competition, Grant Thornton chief among them. But the benefits of buying in early to cloud-based productivity services didn’t stop there for Grant Thornton. So, Swift signed on before the official launch of Microsoft’s Windows 365 Cloud PC roughly one year ago.




















Let's personalize your content