DNS Zone Setup Best Practices on Azure
Cloudera
FEBRUARY 12, 2024
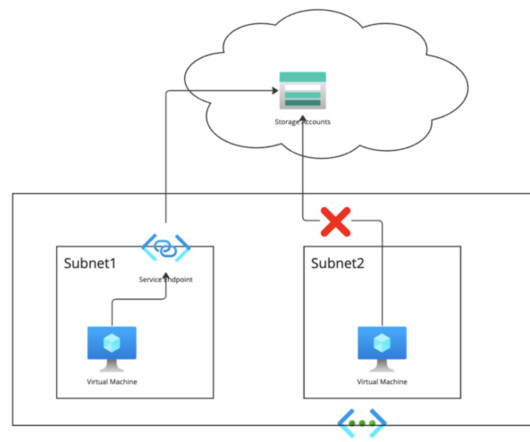
Most users have restrictions on firewalls for wildcard rules. Most users have restrictions on firewalls for wildcard rules. DNS servers are usually deployed in the hub virtual network or an on-prem data center instead of in the Cloudera VNET. There is at present no option to disable private DNS zones for data engineering.























Let's personalize your content