8 questions to answer before your startup faces technical due diligence
TechCrunch
OCTOBER 25, 2022
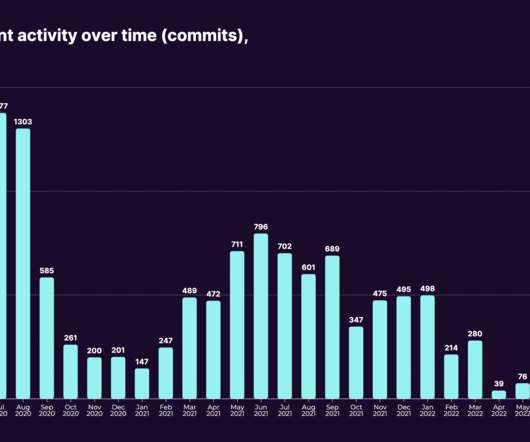
Will your organization and your code pass technical due diligence when it’s your turn? Let’s start with the positives: If an investor is proceeding with technical due diligence (TDD), you’ll likely pass. Here’s the not-so-good news: Companies can pass the business test, but fail TDD.





















































Let's personalize your content