Practical Steps for Enhancing Reliability in Cloud Networks - Part I
Kentik
APRIL 4, 2023
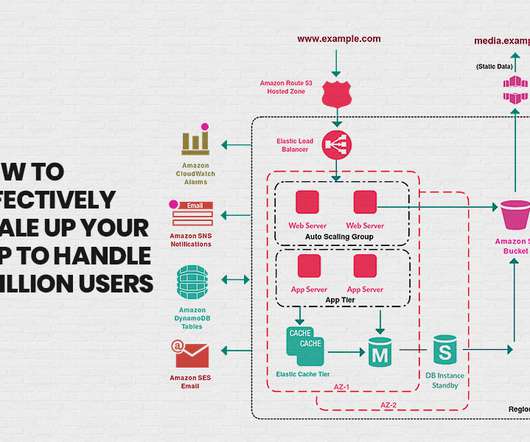
Highly available networks are resistant to failures or interruptions that lead to downtime and can be achieved via various strategies, including redundancy, savvy configuration, and architectural services like load balancing. Resiliency. Resilient networks can handle attacks, dropped connections, and interrupted workflows. Durability.



































Let's personalize your content