The Hidden Gem of Savings in the Software Delivery. And no, it’s not AI
CIO
MARCH 11, 2024
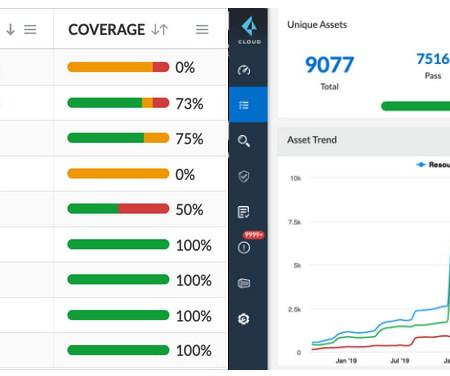
According to Deloitte research , AI will boost the productivity of software development processes from 50% to 1000%. It will improve project management, help with requirements creation, assist developers with coding, cover the system with auto-tests, report defects, and improve deployment.


















































Let's personalize your content