Infrastructure Engineer: Key Duties, Skills, and Background
Altexsoft
JULY 4, 2022
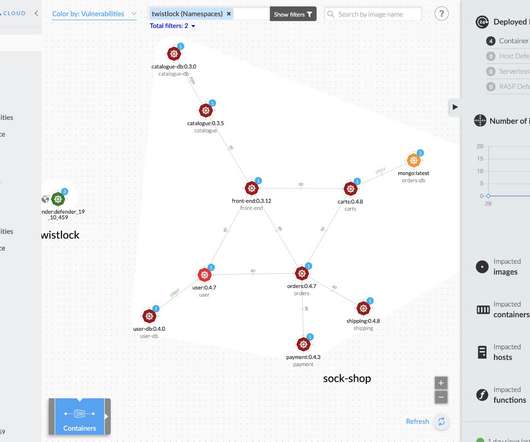
Infrastructure is quite a broad and abstract concept. Companies often take infrastructure engineers for sysadmins, network designers, or database administrators. What is an infrastructure engineer? (80, Key components of IT infrastructure. This environment or — infrastructure — consists of three layers.



























Let's personalize your content