5 best practices for securing Kubernetes runtime workloads
Lacework
APRIL 12, 2023
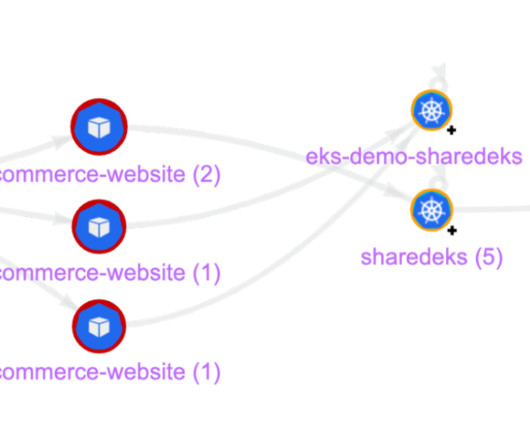
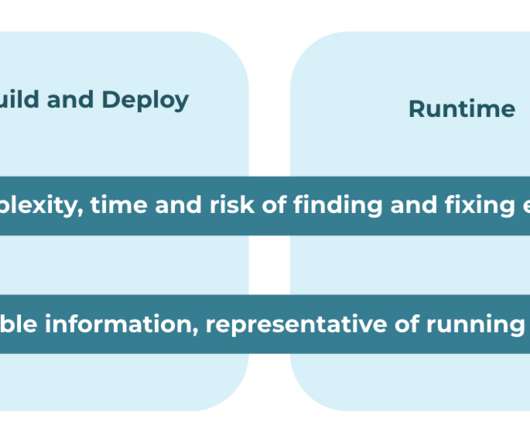
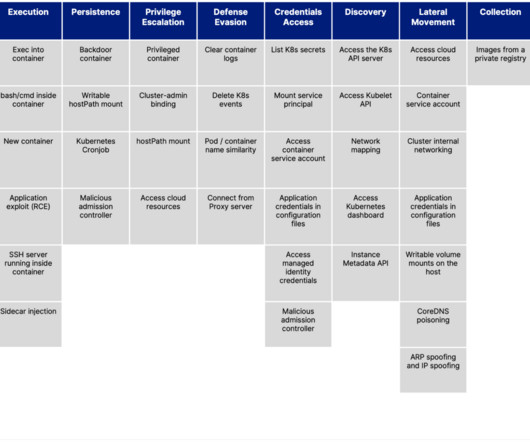
While hardening Kubernetes workload configuration or Kubernetes Role-Based Access Controls (RBAC) is a necessary best practice, it is just the tip of the iceberg when securing Kubernetes clusters. The Red Hat 2022 State of Kubernetes […] The Red Hat 2022 State of Kubernetes […]





























Let's personalize your content