How Secure Is VoIP Compared to Landline Phone?
Strategy Driven
NOVEMBER 18, 2022
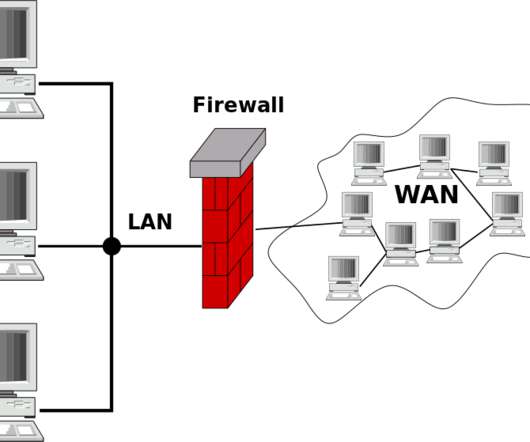
However, because more and more people are turning to VoIP systems, it has become much easier to install specific security features that can improve the experience. So is a VoIP actually more secure than a landline phone? Are Landlines More Secure Than VoIPs? Why Are VoIPs Easier To Hack? Are Any VoIPs Secure?































Let's personalize your content