Build a read-through semantic cache with Amazon OpenSearch Serverless and Amazon Bedrock
AWS Machine Learning - AI
NOVEMBER 26, 2024
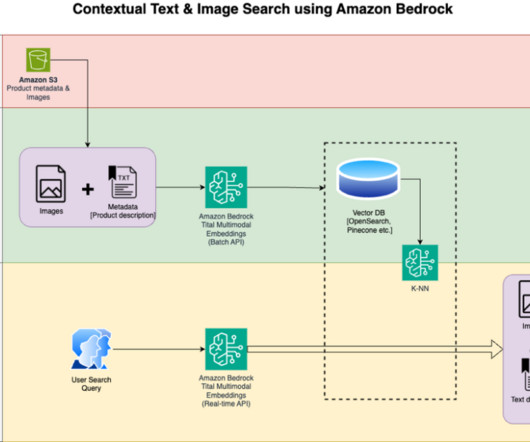
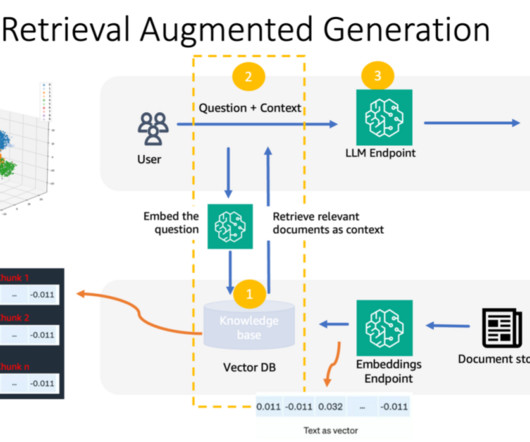
Given the increasing need for efficient and cost-effective AI solutions, we present a serverless read-through caching blueprint that uses repeated data patterns. With OpenSearch Serverless, you can establish a vector database suitable for setting up a robust cache system.













































Let's personalize your content