Threat Alert: Threat Actors Using release_agent Container Escape
Aqua Security
NOVEMBER 3, 2021
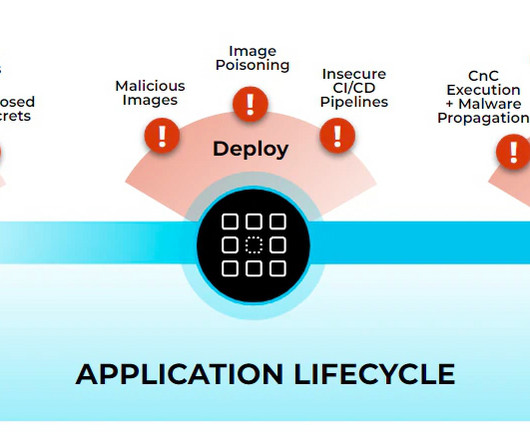
As part of the campaign, the threat actors used a container escape technique that leverages the CGroup release_agent feature. This technique allows an attacker to break out from the container and compromise the host and, potentially, the entire network of an organization.






















Let's personalize your content