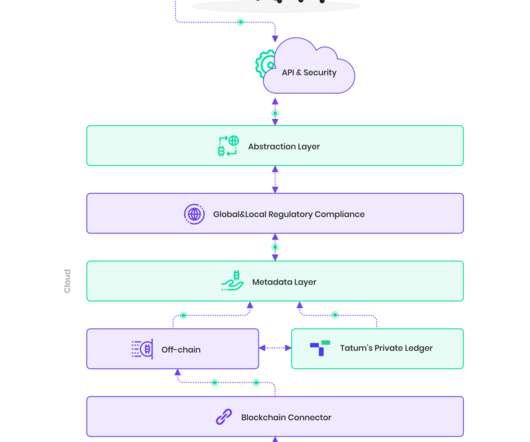
Tatum lets you interact with blockchains using API calls
TechCrunch
SEPTEMBER 21, 2021
This is the easy part, as it basically comes down to spinning up a Linux server, installing a package and running this client. Blockchain is like the internet in 1997. Kobelka has a background in banking infrastructure. I’ve spent over 15 years in banking as a technical core banking expert,” he told me.

































Let's personalize your content