Generative AI: 5 enterprise predictions for AI and security — for 2023, 2024, and beyond
CIO
OCTOBER 25, 2023
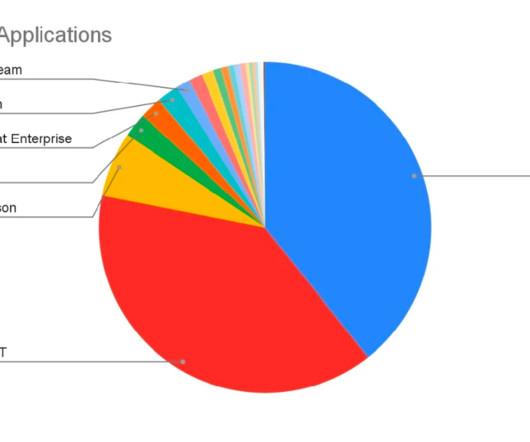
Our recent data analysis of AI/ML trends and usage confirms this: enterprises across industries have substantially increased their use of generative AI, across many kinds of AI tools. Interestingly, Drift holds the distinction of being the most blocked, as well as most used, AI application. These are questions enterprises must answer.
































Let's personalize your content