Are you compromising data privacy with your security vendor?
Lacework
SEPTEMBER 27, 2023
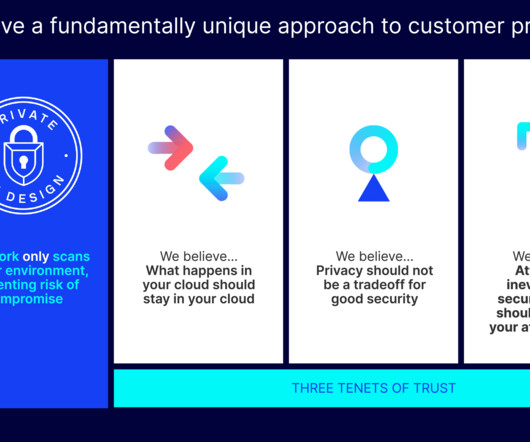
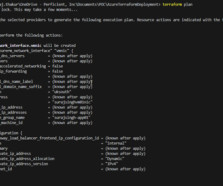
So, of course, all cloud security vendors prioritize these aspects, right? What happens in your cloud should stay in your cloud Which permissions have you granted your vendor? Your cloud, your data. Do you know which permissions you’ve granted your cloud security vendor? Unfortunately, that’s not the case.




























Let's personalize your content