The need for DevSecOps in the embedded world
Xebia
DECEMBER 16, 2022
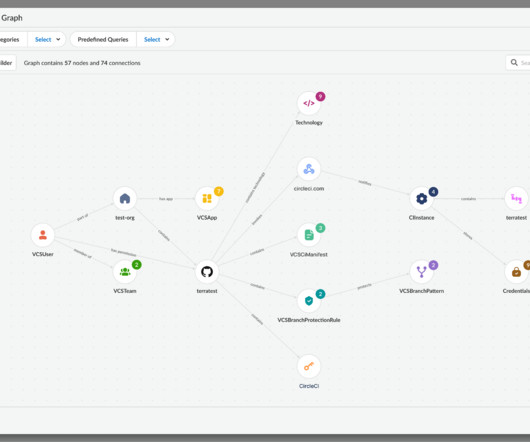
Have you ever wondered why the embedded development industry is behind others when it comes to security? Or how web application developers improved their security maturity over the years? As I started gaining experience in the embedded security industry, I started seeing patterns emerge in the vulnerabilities I discovered.

































Let's personalize your content