What is CI/CD? Continuous integration and continuous delivery explained
InfoWorld
APRIL 1, 2024
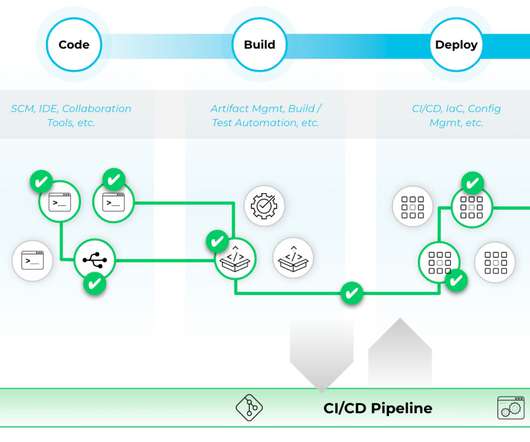
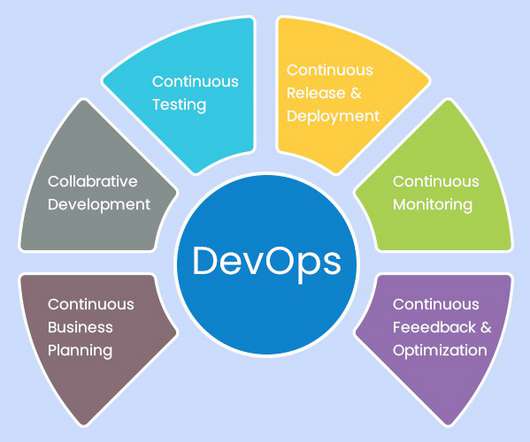
Continuous integration (CI) and continuous delivery (CD), also known as CI/CD, embodies a culture and set of operating principles and practices that application development teams use to deliver code changes both more frequently and more reliably. What does CI/CD stand for? CI/CD is a best practice for devops teams.















































Let's personalize your content