Finding your ideal VMware Disaster Recovery and Migration Cloud Provider
CIO
SEPTEMBER 23, 2022
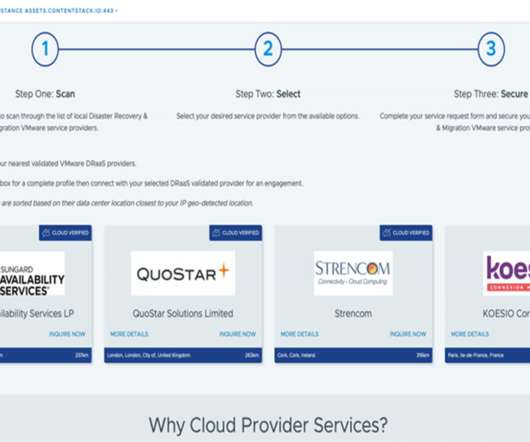
Did you know that evaluating, selecting, and purchasing B2B software can be a long cycle with an average of 3-6months being the minimal time spent on this process? Step 1: Scan : Visit your vSphere console to scan through the list of local Disaster Recovery & Migration VMware Cloud Providers.




















































Let's personalize your content