Modernizing applications: the importance of reducing technical debt
CIO
APRIL 27, 2023
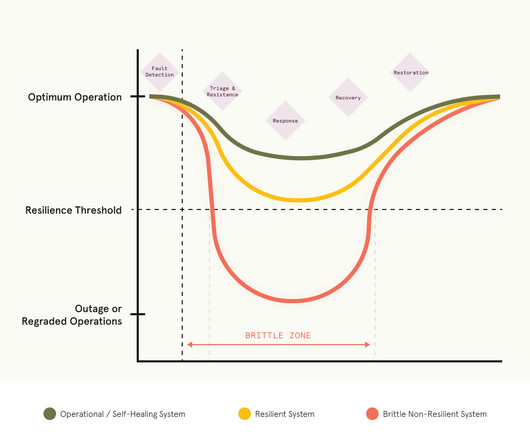
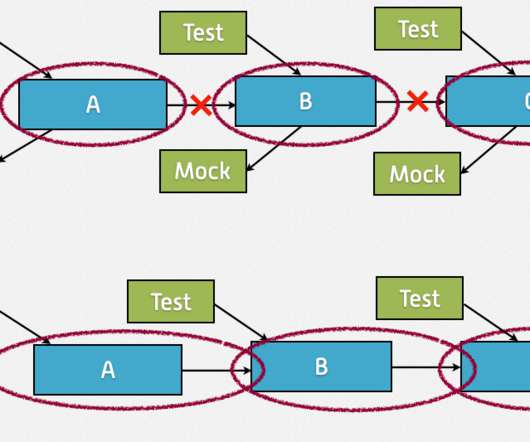
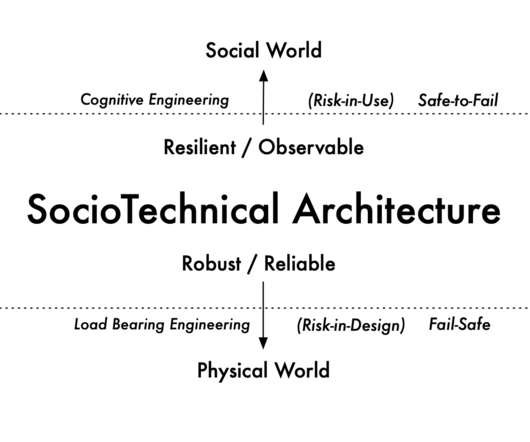
Technical debt is no longer just a “technical” problem. As recent, widely publicized events have shown, it is a business problem that can have serious consequences for organizations. What is technical debt? The warning signs of technical debt are clear.













































Let's personalize your content