Zero Trust Network for Microservices With Istio
Dzone - DevOps
APRIL 23, 2023
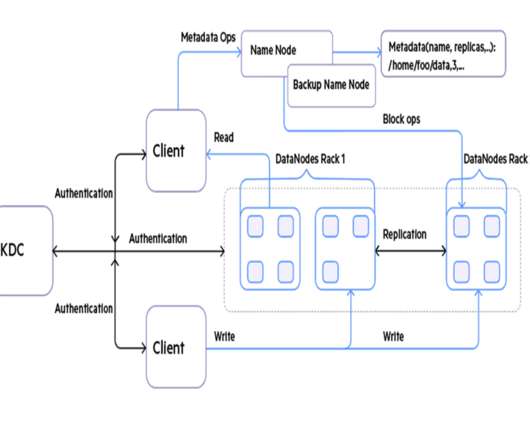
It means securing the network perimeter and access control using firewalls. With the advent of microservices architecture, static and network-based perimeters are no longer effective. Zero trust network (ZTN) is a different approach to secure data across cloud-based networks.












































Let's personalize your content