14 in-demand cloud roles companies are hiring for
CIO
DECEMBER 22, 2023
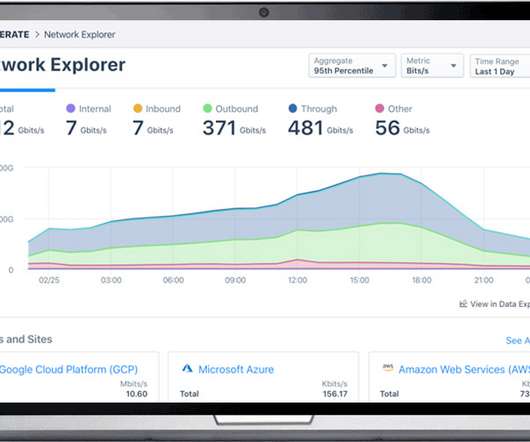
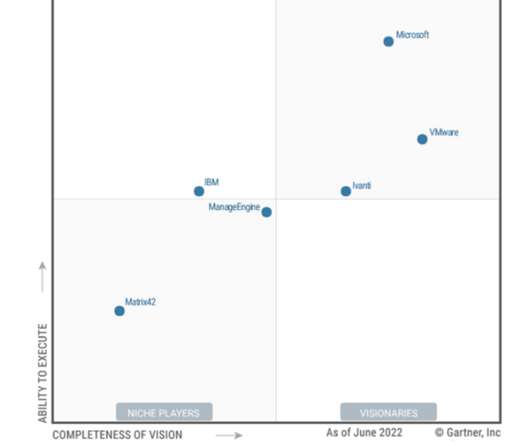
After marked increase in cloud adoption through the pandemic, enterprises are facing new challenges, namely around the security, maintenance, and management of cloud infrastructure. These IT pros can also help organizations avoid potential risks around cloud security, while ensuring a smooth transition to the cloud across the company.



































Let's personalize your content