A small open-source story
Marcusoft
MARCH 25, 2024
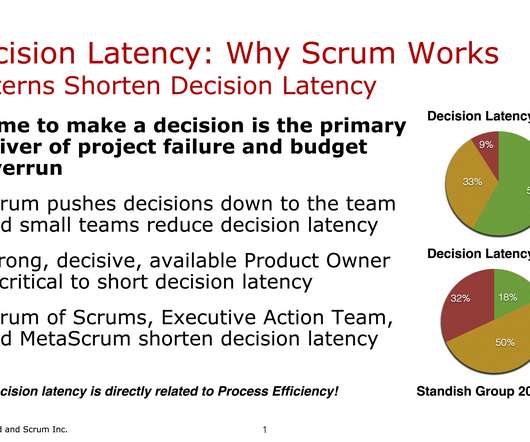
Back in 2010, I was very interested in BDD (Behaviour-driven Development) as a stepping stone into agile testing-thinking as a general great tool to foster better conversations. They sent a consultant to our team to see if we could make use of it. I want to emphasize that I’m not a good role model for open-source maintainers.



















































Let's personalize your content