Four Priorities for Better Endpoint Management in 2020
Kaseya
JANUARY 23, 2020
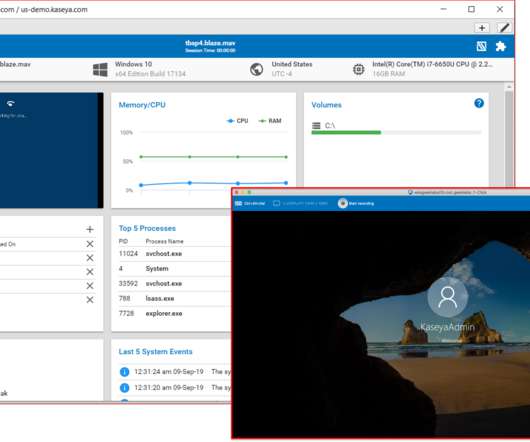
Endpoint Backup and Recovery . Kaseya Unified Backup . Kaseya Unified Backup (KUB) enables IT technicians to manage endpoints, monitor network devices, and perform backup and recovery tasks, all from a single pane of glass i.e. from Kaseya VSA, the endpoint and network management solution. .



































Let's personalize your content