The Network Also Needs to be Observable, Part 2: Network Telemetry Sources
Kentik
JANUARY 6, 2021
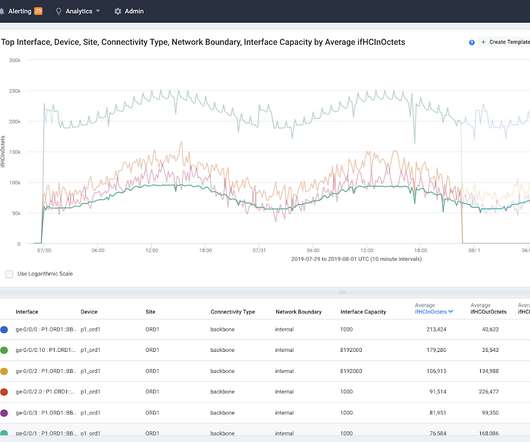
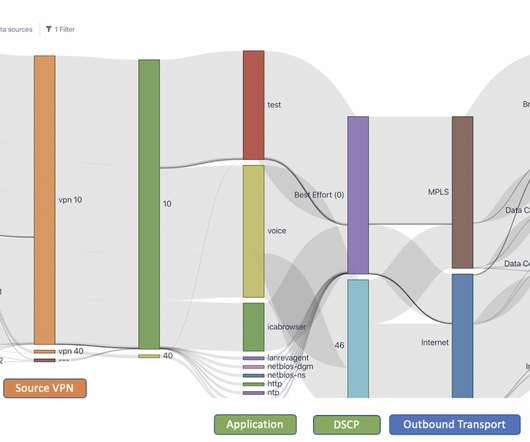
In part 1 of this series , I talked about the importance of network observability as our customers define it — using advances in data platforms and machine learning to supply answers to critical questions and enable teams to take critical action to keep application traffic flowing. Access and transit networks, edge and exchange points, CDNs.

































Let's personalize your content