The GitHub Actions Worm: Compromising GitHub Repositories Through the Actions Dependency Tree
Prisma Clud
SEPTEMBER 14, 2023
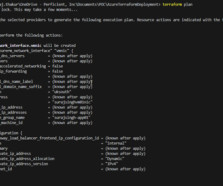
Get an in-depth look at the attack vectors, technical details and a real-world demo in this blog post highlighting our latest research. As the premier platform for hosting open-source projects, GitHub’s popularity has boosted the popularity of its CI/CD platform — GitHub Actions. Reference a tag. Reference a commit hash.


































Let's personalize your content