Managed Services for Enhanced Network Security, Endpoint-to-Endpoint
CIO
JULY 11, 2022
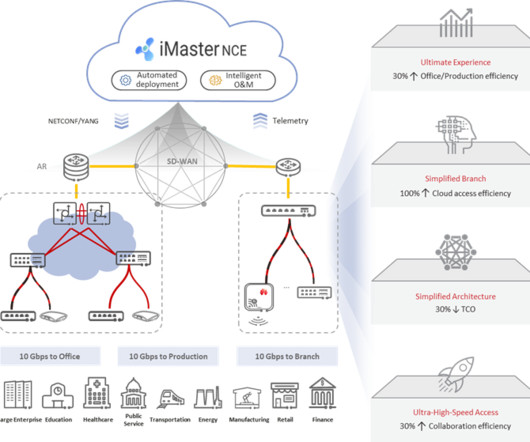
With the proliferation of hybrid clouds, SD-WAN, and a plethora of connected devices and digital platforms, it’s becoming increasingly challenging to ensure end-to-end security is in place. For this reason, many IT leaders will include a mix of fiber, wireless, cable, and DSL for optimal broadband.





































Let's personalize your content