Advanced Persistent Threat Techniques Used in Container Attacks
Aqua Security
AUGUST 26, 2021
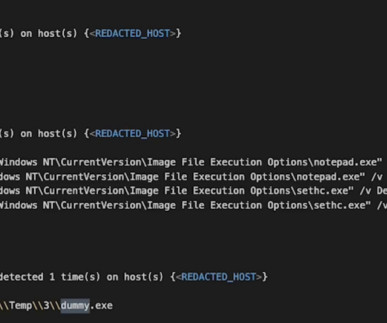
Aqua’s Team Nautilus detected an intensive campaign targeting cloud native environments that uses advanced persistent threat (APT) techniques usually leveraged by nation-state threat actors.

































Let's personalize your content