Top 10 Frameworks for Developing Enterprise Applications
OTS Solutions
JUNE 9, 2023
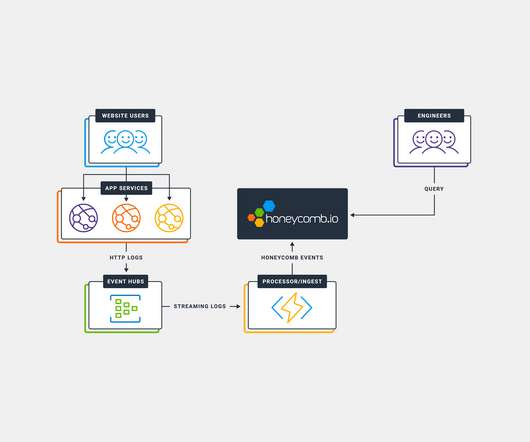
Enterprise application development projects have been transforming all industries such as healthcare, education, travel, hospitality, etc. In this blog, we discuss the top-rated enterprise application development frameworks that make your process of developing an enterprise application easy. billion by 2030.





































Let's personalize your content