Network topologies – A series: Part 1
Xebia
APRIL 18, 2023
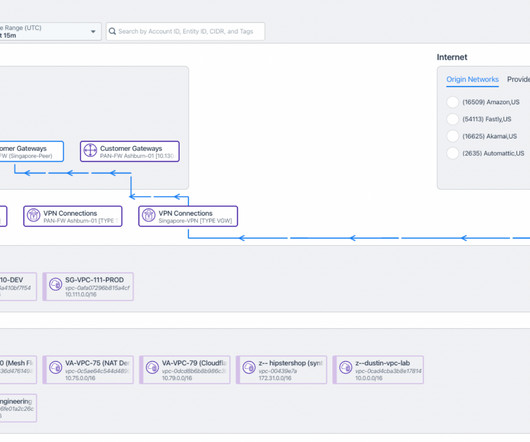
It’s expected that the reader does have some knowledge about basic cloud concepts, such as VPC and firewall rules, or have the ability to find the documentation for this when needed. The examples will be presented as Google Cloud Platform (GCP) resources, but can in most cases be inferred to other public cloud vendors.














































Let's personalize your content