Why endpoint security will be a renewed priority for businesses of all sizes in 2023
CIO
NOVEMBER 23, 2022
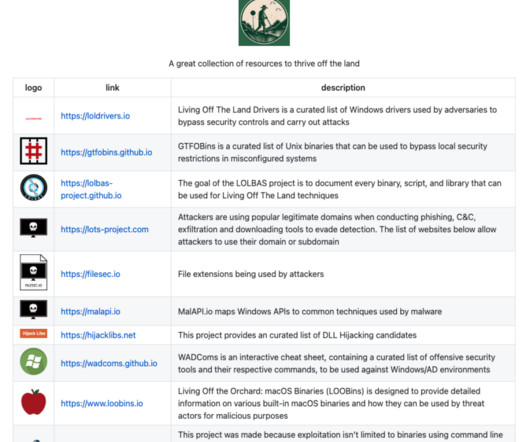
Three of the biggest risks moving into 2023 and beyond are: Ransomware – in which a malicious program infects a computer, locking access to all files until a ransom is paid to gain access to an unlock key. On the hardware layer, Intel boosts the security of devices with total component traceability that starts at the factory floor.








































Let's personalize your content