Types and Functions of Network Interface Card (NIC)
The Crazy Programmer
SEPTEMBER 23, 2021
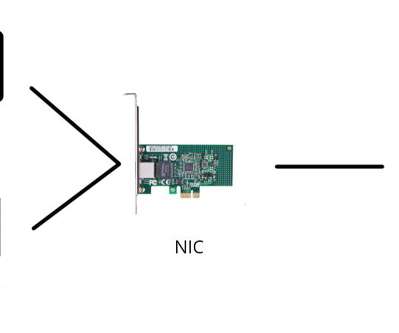
It is the hardware components that can exist internally or externally in the devices that need internet access. These devices control the access of the internet or network communication. The NIC also has other names like Network Interface Controller, LAN Adapter, Connection Card, and Ethernet Card. Wireless Network Connection.

































Let's personalize your content