Azure-Specific Policies to Detect Suspicious Operations in the Cloud Environment
Prisma Clud
APRIL 20, 2023
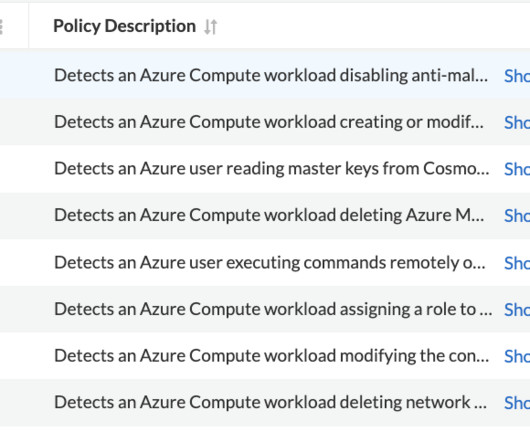
The attacker could then use the permissions of the machine to modify the routing tables in the network and directly access a remote server to perform data exfiltration. Of the eight policies, six focus on activities originating from Azure compute workloads, and the remaining two policies focus on activities originating from Azure users.
































Let's personalize your content