How customers capture real economic value with zero trust
CIO
NOVEMBER 30, 2023
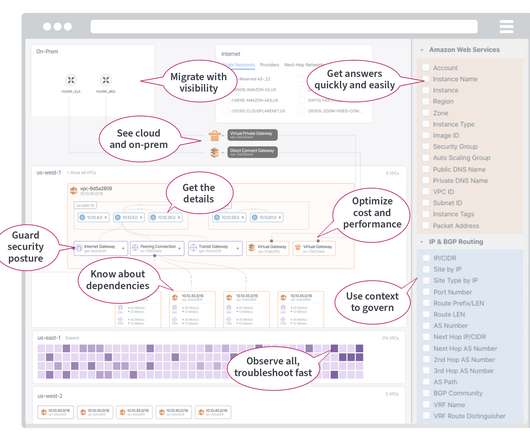
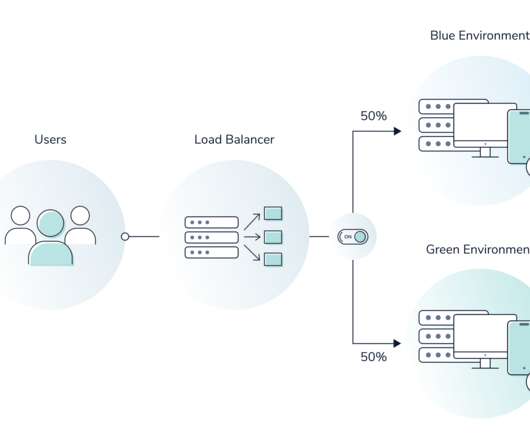
Hub-and-spoke networks and castle-and-moat security architectures were designed for days gone by when users, apps, and data all resided on premises. The Zscaler Zero Trust Exchange provides a different kind of architecture (zero trust) that not only enhances security but reduces costs while doing so.











































Let's personalize your content