Building a SQL Server Virtual Lab in Windows: Create VMs for the SQL Servers
Datavail
JULY 10, 2020
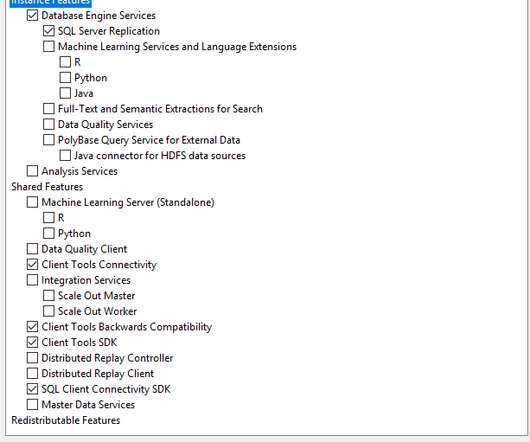
Installing Windows Server 2019. Configuring Windows Firewall. The only difference is on the disk space step where we will allocate 40 GB for the VM instead of 32 GB as we did for the DC as we will installing Windows Server 2019 and SQL Server 2019 on this VM. We will go through the following steps: Creating a VM.










































Let's personalize your content