2023 Unit 42 Attack Surface Threat Report Highlights the Need for ASM
Palo Alto Networks
SEPTEMBER 14, 2023
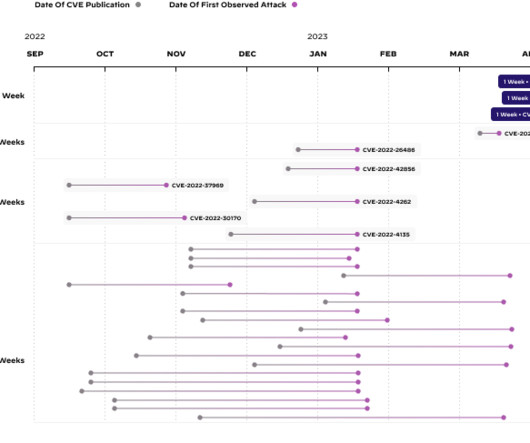
Palo Alto Networks Unit 42 illuminates some of the riskiest security observations around attack surface management (ASM) with the 2023 Unit 42 Attack Surface Threat Report. The report contrasts the dynamic nature of cloud environments with the speed at which threat actors are exploiting new vulnerabilities.





























Let's personalize your content