From Excavators to Earthquakes: Achieving Redundant Networks
Megaport
MAY 24, 2021
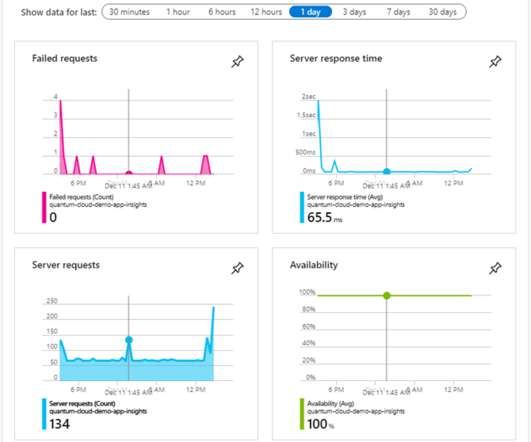
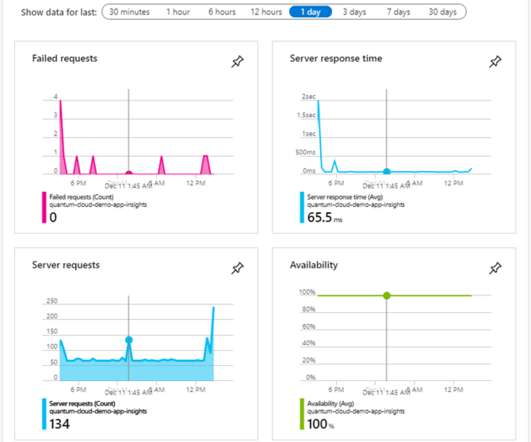
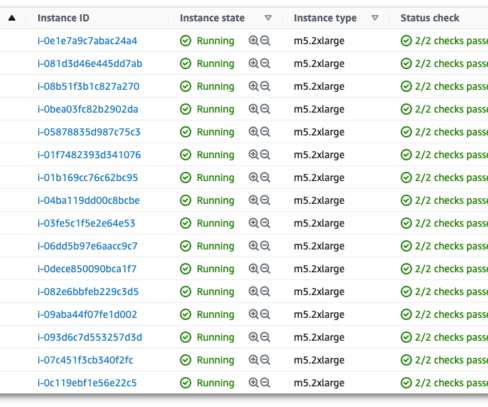
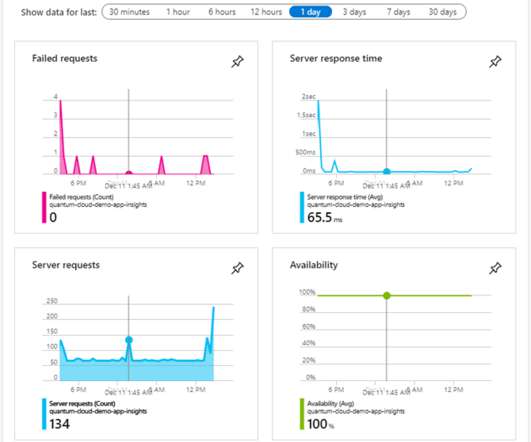
In March, the world turned its attention to France as a fire destroyed several data centers, disrupting millions of websites and businesses in the process. It’s easy to forget that the internet, and the cloud, rely on physical infrastructure, but this event was an abrupt reminder.
















































Let's personalize your content