APM for All: Simplifying the Complexity of Cloud
DevOps.com
JANUARY 2, 2020
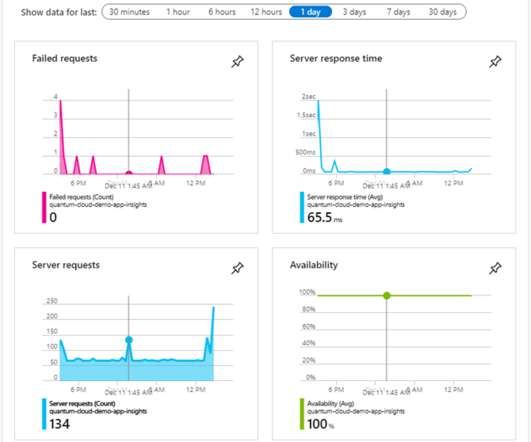
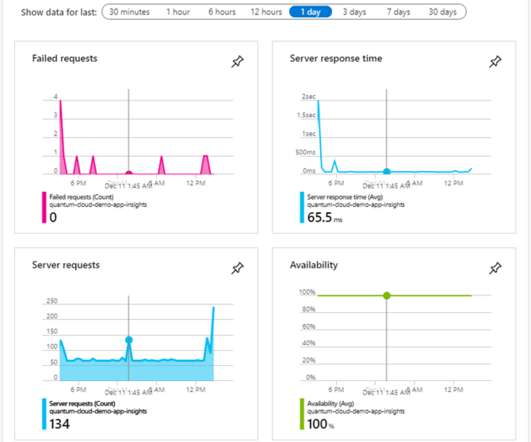
As companies adopt hybrid and even multi-cloud strategies, their IT departments are beginning to use dynamic technologies to build new application features on top of existing back-end business systems. Most organizations now have a blended, multi-cloud architecture where public clouds are integrated with the existing on-premises, private or hybrid cloud infrastructure and applications.








































Let's personalize your content