Due diligence is ever more critical as the battle for cloud sovereignty intensifies
CIO
DECEMBER 21, 2022
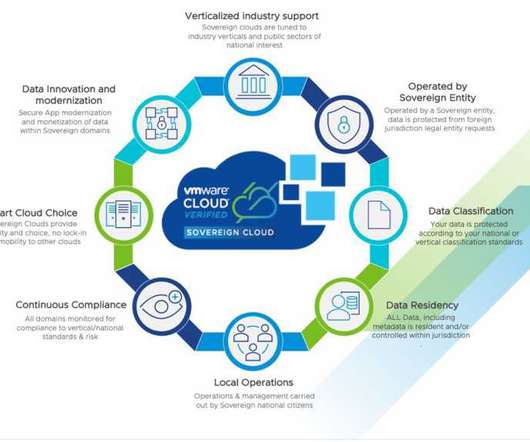
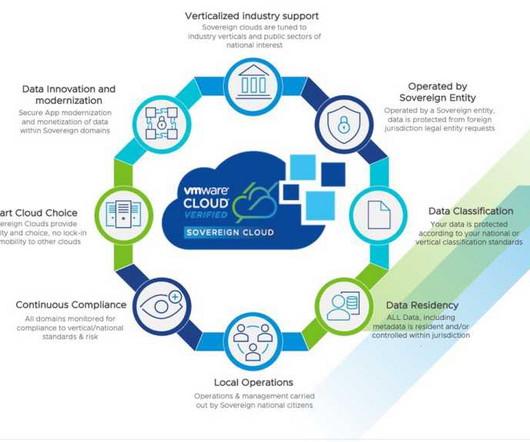
This is where VMware’s strategy is unique: VMware encourages multi-cloud and helps organizations maintain a cloud strategy that avoids lock-in and maintains quality and security while monitoring performance. Some also innovate solutions for secure data exchange to enable monetizing your data, a critical component in the growing data market.














































Let's personalize your content