How to Conduct User Acceptance Testing: Process Stages, Deliverables, and End-User Testing Place in Quality Assurance
Altexsoft
JUNE 26, 2019
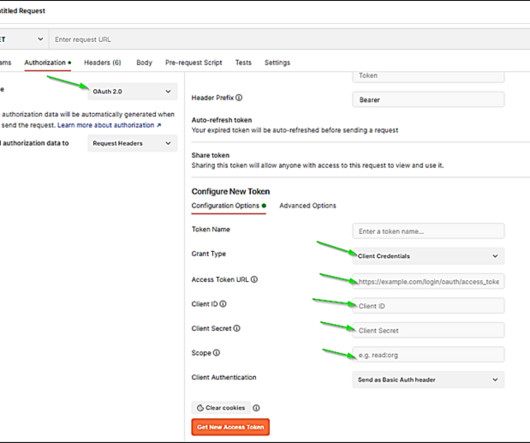
When conducting various quality assurance activities , development teams are able to look at the product from the user’s standpoint. What is user acceptance testing and how is it different from quality assurance? Authentication is not needed. Add any product to a shopping cart. Proceed to the shopping cart.



































Let's personalize your content