CIO Confidential: What Keeps CIOs and IT Leaders Up at Night
CIO
NOVEMBER 8, 2022
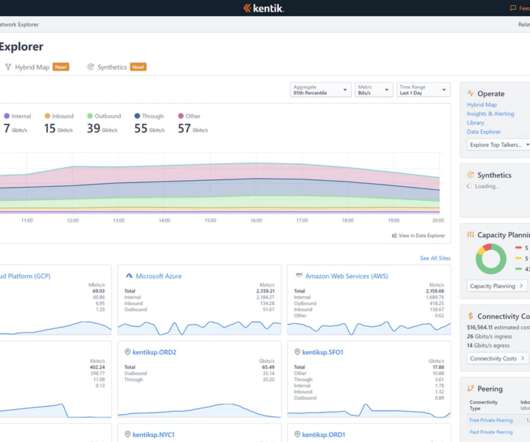
To get to the heart of these pain points, we sat down with CIOs and IT leaders across industries to candidly discuss where they are in their digital transformation journeys, the emerging infrastructure technologies they’re using, and their biggest fears and pressures when it comes to the future of their business.




































Let's personalize your content