5 reasons to move to a network platform
CIO
FEBRUARY 27, 2024
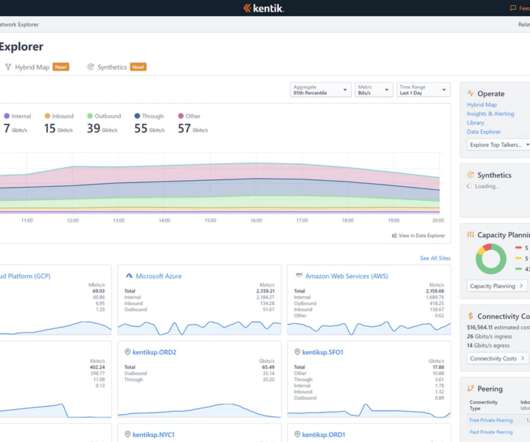
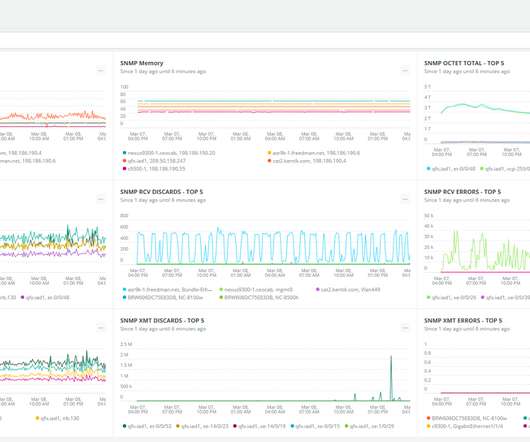
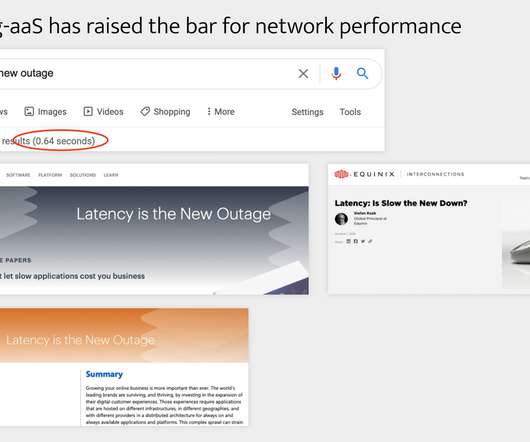
In today’s era of dynamic disruption, IT leaders are taking center stage in navigating a complex and vast network. On top of that, how do you build a resilient network that can protect your people, systems, and data from external threats? The answer is the network platform. Navigating these complexities can be challenging.

















































Let's personalize your content